Annex B
Dated September 2025.
DATA PROTECTION AGREEMENT
This Data Protection Agreement (“DPA”) is entered into by and between Open Web Technologies Ltd. and / or any of its affiliates, as applicable (“Company”), and the legal entity that entered into an agreement with Company (“Recipient” and the “Agreement”, respectively). This DPA reflects the parties’ agreement with regard to the Personal Data disclosed to or processed by the Recipient for the provisions of the services outlined in the Agreement. Both Parties shall be referred to as the “Parties” and each, a “Party”. This DPA is entered into by Company and Recipient and supplements the Agreement. This DPA will be effective, and shall replace any previously applicable terms relating to its subject matter, from the Agreement Effective Date.
If you are accepting this DPA on behalf of Recipient, you warrant that: (a) you have full legal authority to bind Recipient to this DPA; (b) you have read and understood this DPA; and (c) you agree, on behalf of Recipient, to this DPA. If you do not have the legal authority to bind Recipient, please do not accept this DPA.
- Introduction
- This DPA reflects the Parties’ agreement on the processing of Personal Data in connection with the Data Protection Laws.
- Any ambiguity in this DPA shall be resolved to permit the Parties to comply with all Data Protection Laws.
- In the event and to the extent that the Data Protection Laws impose stricter obligations on the Parties than under this DPA, the Data Protection Laws shall prevail.
- Definitions And Interpretation
- In this DPA:
- “Approved Jurisdiction” means a jurisdiction approved as having adequate legal protections for data by the European Commission (currently found here), the UK Information Commissioner's Office (currently available here), or the Swiss Federal Data Protection and Information Commissioner ("FDPIC")(currently available here), all as applicable.
- “Data Protection Laws” means any and all applicable domestic and foreign laws, rules, directives and regulations, on any local, provincial, state, federal or national level, pertaining to data privacy, data security or the protection of Personal Data, including the Privacy and Electronic Communications Directive 2002/58/EC (and respective local implementing laws) concerning the processing of personal data and the protection of privacy in the electronic communications sector (Directive on privacy and electronic communications), UK's Privacy and Electronic Communications Regulations 2003 (PECR), Regulation (EU) 2016/679 of the European Parliament and of the Council of 27 April 2016 on the protection of natural persons with regard to the processing of personal data and on the free movement of such data (“GDPR”), Data Protection Act 2018 and the GDPR as it forms part of the law of England and Wales, Scotland and Northern Ireland by virtue of section 3 of the European Union (Withdrawal) Act 2018 ("UK GDPR"), the Swiss Federal Act on Data Protection (“FADP”), US Data Protection Laws, and any amendments or replacements to the foregoing.
- “Data Subject” means a natural person to whom Personal Data relates.
- “Security Incident“ shall mean any accidental or unlawful destruction, loss, alteration, unauthorized disclosure of, or access to, Personal Data. For the avoidance of doubt, any Personal Data Breach (as defined in the GDPR) or other equivalent terms under Data Protection Laws will comprise a Security Incident.
- “Special Categories of Data“ means personal data as defined under Article 9 of the GDPR and where applicable, "Sensitive Personal Information" or "Sensitive Data" under US Data Protection Laws.
- “Standard Contractual Clauses” means the applicable Module of the standard contractual clauses for the transfer of personal data to third countries pursuant to Regulation (EU) 2016/679 of the European Parliament and of the Council from June 4th 2021, as available here: https://eur-lex.europa.eu/legal-content/EN/TXT/HTML/?uri=CELEX:32021D0914&from=EN.
- "UK Addendum" means the International Data Transfer Addendum to the EU Commission Standard Contractual Clauses, which entered into force on 21 March, 2022, as available here: https://ico.org.uk/for-organisations/uk-gdpr-guidance-and-resources/international-transfers/international-data-transfer-agreement-and-guidance/.
- “US Data Protection Laws” means, any and all applicable acts, directive, decrees, laws, rules, and regulations, and binding regulatory guidance, on any state or federal level, pertaining to data privacy, data security and the protection of Personal Data, including, without limitation, in California, Colorado, Connecticut, Utah, Virginia, Texas, Oregon, Florida, Montana, Iowa, Delaware, New Jersey, New Hampshire, Nebraska, Tennessee, and Minnesota, as well as any future laws, amendments, or regulations that may be enacted or promulgated governing data protection within the United States.
- The terms “Controller”, “processing”, "Personal Data", and “Processor” as used in this DPA have the meanings given to them in Data Protection Laws. Where applicable, a controller shall be deemed a “Business“ and a processor shall be deemed to be a “Service Provider“ or a "Contractor", and Personal Data shall be deemed to be "Personal Information", as these terms are defined under US Data Protection Laws.
- Any reference to a legal framework, statute or other legislative enactment is a reference to it as amended or re-enacted from time to time.
- In this DPA:
- Application Of This DPA
- This DPA will only apply to the extent all of the following conditions are met:
- Recipient processes Personal Data that is made available by Company in connection with the Agreement;
- Any of the Data Protection Laws apply to the processing of Personal Data.
- This DPA will only apply to the extent all of the following conditions are met:
- Roles And Restrictions On Processing
- Independent Controllers. Each Party:
- is an independent controller of Personal Data under the Data Protection Laws;
- as required under the Data Protection Laws, maintain accurate written records of all the processing activities conducted by that Party in relation to any Personal Data for the purposes of performing its respective obligations under the Agreement;
- will individually determine the purposes and means of its processing of Personal Data;
- will be responsible to ensure that any Personal Data collected and processed by such Party is accurate and remains accurate for the duration of its processing;
- will comply with the obligations applicable to it under the Data Protection Laws with respect to the processing of Personal Data;
- will be responsible to exercise and respond to any requests by data subjects to exercise their rights under Data Protection Law, including (but not limited to) Articles 15-22 of the GDPR (“Data Subject Rights”), and shall provide reasonable cooperation and assistance to the other Party in connection with exercising Data Subject Rights;
- will promptly notify the other Party of any circumstances in which such Party is unable or becomes unable to comply with this DPA or Data Protection Laws, or any actual or potential changes to Data Protection Laws, if this shall affect the other Party’s ability to comply with its obligations under this DPA or Data Protection Laws.
- Restrictions on Processing. Section 4.1 (Independent Controllers) will not affect any restrictions on either Party’s rights to use or otherwise process Personal Data under the Agreement.
- Disclosure of Personal Data. In performing its obligations under the Agreement, the Recipient shall process Personal Data provided by Company: (i) only for the purposes set forth in the Agreement or as otherwise agreed to in writing by the Parties, provided such processing strictly complies with (a) Data Protection Laws, and (b) Recipient's obligations under the Agreement (the “Permitted Purposes”) and provided that Recipient will not do or permit any act or omission which would cause Company to incur any liability under Data Protection Laws; and (ii) and shall, if requested by Company, securely delete or return the copies of the disclosed Personal Data to Company, cease the processing of the disclosed Personal Data, and shall certify to Company to that effect, unless and only insofar as the processing of the Personal Data is required for the fulfillment of the Permitted Purposes or is permissible under Data Protection Laws, in which case the Recipient will inform Company of any such requirement and only further process the Personal Data as necessary to comply with the foregoing.
- Privacy Frameworks, Consent and Opt-Out Signals. Recipient shall comply with, and shall contractually require any of its applicable partners (such as advertisers and vendors) to comply with IAB frameworks (such as IAB TCF and GPP), and will promptly comply, and shall cause any of its applicable partners to comply, with any end user's preference, opt-out or withdrawal of consent signals transmitted to Recipient via Company's or its partners’ consent mechanisms, or which are transmitted to it in any other manner, as applicable.
- Lawful grounds and transparency. Each Party shall maintain a publicly-accessible privacy notice that satisfies transparency disclosure requirements of Data Protection Laws, and warrants and represents that it has provided Data Subjects with appropriate transparency regarding data collection and use and all required notices, in accordance with Data Protection Law, including Articles 13 and 14 of the GDPR. Both Parties will cooperate in good faith in order to identify the information disclosure requirements and each party hereby permits the other Party to identify it in the other Party’s privacy policy, and to provide a link to the other Party’s privacy policy in its privacy policy.
- Subcontracting. Where either Party subcontracts the processing activities of Personal Data contemplated herein to a third party, it shall ensure that such third party enters into written contractual obligations which are (in the case of a third party controller) no less onerous than those imposed by this DPA or (in the case of a third party processor) compliant with Article 28 of the GDPR. Each Party shall be liable for the acts or omissions of its subcontractors to the same extent it is liable for its own actions or omissions under this DPA.
- Independent Controllers. Each Party:
- Personal Data Transfers
- Where the GDPR, the FADP, or UK GDPR are applicable, either Party may transfer Personal Data outside the European Economic Area ("EEA"), Switzerland, UK or an Approved Jurisdiction, subject to one of the appropriate safeguards in Article 46 of the GDPR (or the equivalent clause of the UK GDPR) and Section 3 of the FADP, as applicable.
- Where the GDPR, the FADP, or UK GDPR are applicable, to the extent that Recipient processes Personal Data outside the EEA, UK, Switzerland, or an Approved Jurisdiction (as applicable), then the Parties shall be deemed to enter into module 1 of the Standard Contractual Clauses or the UK Addendum, as applicable, subject to any amendments contained in Annex I, in which event: (i) the Standard Contractual Clauses or the UK Addendum, as applicable, are incorporated herein by reference; and (ii) Company shall be deemed as the data exporter and the Recipient shall be deemed as the data importer(as these terms are defined therein).
- If Recipient intends to rely on Standard Contractual Clauses including, where applicable the UK Addendum, then if the Standard Contractual Clauses or the UK Addendum are superseded by new or modified mechanism, the new or modified mechanism shall be deemed to be incorporated into this DPA, and Recipient will promptly begin complying with such mechanism. Recipient will abide by the obligations set forth under the Standard Contractual Clauses and UK Addendum.
- Unless stated otherwise, in case of a conflict between the provisions of the Data Protection Addendum to the provisions of the Standard Contractual Clauses and the UK Addendum, the provisions providing the more stringent protection to Personal Data and the rights of individuals shall govern. For the avoidance of doubt, any changes required under the Standard Contractual Clauses or UK Addendum, shall only apply to the processing of Personal Data which is subject to the GDPR, the FADP, or UK GDPR (as applicable).
- Protection Of Personal Data
- The Parties will provide a level of protection for Personal Data that is at least equivalent to that required under Data Protection Laws. Recipient shall implement appropriate technical and organizational measures to protect the Personal Data, as detailed in Annex III.
- If a Party suffers a confirmed Security Incident with respect to Personal Data disclosed from the other Party, such Party shall notify the other Party without undue delay and the Parties shall cooperate in good faith to agree and action such measures as may be necessary to mitigate or remedy the effects of the Security Incident. If a Party suffers a confirmed Security Incident, then such Party shall be responsible to notify the supervisory authority or the Data Subjects with respect to such Security Incident, as required under Data Protection Laws.
- Mutual Assistance
- Each Party shall:
- appoint at least one representative as point of contact and responsible manager for all issues arising out of the Data Protection Laws (a "Designated Representative"); the Designated Representative(s) of both Parties will work together in good faith to reach an agreement with regards to any issues arising from time to time in relation to the processing of Personal Data in connection with the Agreement and this DPA;
- use reasonable measures to consult with the other Party about any notices given to Data Subjects in relation to the processing of Personal Data under the Agreement;
- inform the other Party (without undue delay) in the event that it receives a Data Subject request related solely and exclusively to the other Party's respective processing activities and provide all reasonable assistance to ensure Data Subject requests are completed within the timeframe set out in Data Protection Laws;
- provide the other Party with reasonable assistance (having regard to the data available to it) to enable the other Party to comply with any Data Subject request received by the other Party and to respond to any other queries or complaints from Data Subjects;
- provide the other Party with such assistance as the other Party may reasonably request from time to time to enable the other Party to comply with its obligations under the Data Protection Laws including (without limitation) in respect of security, breach notifications, impact assessments and consultations with supervisory authorities or other regulators;
- provide the other Party with such information as it may reasonably request in order to: (a) monitor the technical and organizational measures being taken to ensure compliance with the Data Protection Laws, or (b) satisfy any legal or regulatory requirements, including information reporting, disclosure and other related obligations to any regulatory authority from time to time;
- in the event of an actual or potential Security Incident which does or is reasonably likely to affect the respective processing activities of both Parties, liaise with the other Party in good faith to consider what action is required to resolve the issue in accordance with the Data Protection Laws, and provide such reasonable assistance as is necessary to the other Party to facilitate the handling of such Security Incident in an expeditious and compliant manner.
- Each Party shall:
- Obligations Under The US Privacy Laws
- To the extent that Recipient processes Personal Data which is subject to US Data Protection Laws:
- Recipient shall comply with US Data Protection Laws with respect to the Personal Data that Company makes available to Recipient, including by providing the same level of privacy protection as required of businesses by the US Data Protection Laws;
- Recipient acknowledges that Company has the legal duty and right to take reasonable and appropriate steps to ensure that Recipient processes Personal Data shared with it under the Agreement in a manner consistent with its obligations under US Data Protection Laws and this DPA;
- Recipient must notify Company immediately if Recipient can no longer comply with the obligations set by US Data Protection Laws and this DPA;
- Upon notice from Company of its reasonable belief that Recipient is processing Personal Data in an unauthorized manner, Recipient shall cooperate with the Company in good faith to promptly stop or remediate the unauthorized use of such Personal Data, as necessary in Company’s sole reasonable discretion, including by allowing for audits and inspections by Company (or its authorized auditors) or providing documentation verifying Recipient’s practices;
- Company may require Recipient to attest that it treats the Personal Data made available to it under the Agreement, in the same manner that the Company is obligated to treat it under US Data Protection Laws;
- Company may require Recipient to provide documentation that verifies that Recipient no longer retains or uses the Personal Data of consumers who have had their requests to opt-out forwarded to it by the Company.
- Recipient acknowledges and understands its obligations under this clause, and will comply with them.
- To the extent that Recipient processes Personal Data which is subject to US Data Protection Laws:
- Resolution Of Disputes With Data Subjects Or Supervisory Authorities
- If either Party is the subject of a claim by a Data Subject or a supervisory authority or receives a notice or complaint from a supervisory authority relating to its respective processing activities under the Agreement (a "DP Claim"), it shall promptly inform the other Party of the DP Claim and provide the other Party with such information as it may reasonably request regarding the DP Claim.
- Where the DP Claim concerns the respective processing activities of one Party only, then that Party shall assume sole responsibility for disputing or settling the DP Claim.
- Where the DP Claim concerns the respective processing activities of both Parties, then the Parties shall use all reasonable endeavors to cooperate with a view to disputing or settling the DP Claim in a timely manner; provided always that neither Party shall make any admission or offer of settlement or compromise without using all reasonable endeavors to consult with the other Party in advance.
- Priority
- If there is any conflict or inconsistency between the terms of this DPA and the remainder of the Agreement then, the terms of this DPA will govern. Subject to the amendments in this DPA, the Agreement remains in full force and effect.
- Changes to this DPA.
- No changes, modifications or amendments to this DPA shall be valid or binding unless made in writing and signed by both Parties.
- If any of the Data Protection Laws are superseded by new or modified Data Protection Laws (including any decisions or interpretations by a relevant court or governmental authority relating thereto), the new or modified Data Protection Laws shall be deemed to be incorporated into this DPA, and each Party will promptly begin complying with such Data Protection Laws in respect of its respective processing activities.
Annex I – SCC
- This Annex I sets out the Parties' agreed interpretation of their respective obligations under Module One of the Standard Contractual Clauses.
- The Parties agree that for the purpose of transfer of Personal Data between the Company (Data Exporter) and the Recipient (Data Importer), the following shall apply:
- Clause 7 of the Standard Contractual Clauses shall not be applicable.
- In Clause 11, data subjects shall not be able to lodge a complaint with an independent dispute resolution body.
- In Clause 13, the supervisory authority shall be the Irish Data Protection Commissioner.
- In Clause 17, option 1 shall apply. The Parties agree that the clauses shall be governed by the laws of Ireland.
- In Clause 18(b) the Parties choose the courts of Dublin, Ireland.
- To the extent the UK Addendum applies, the following shall apply as well:
- All the information provided under the Standard Contractual Clauses shall apply to the UK Addendum with the necessary changes per the requirement of the UK Addendum. Annexes 1A, 1B and 2 to the UK Addendum shall be replaced with Annexes I–II below, respectively.
- In Table 4 of the UK Addendum, either party may terminate the agreement in accordance with section 19 of the UK Addendum.
- By entering into this DPA, the Parties hereby agree to the format changes made to the UK Addendum.
- To the extent the FADP applies, the following shall apply:
- References to the GDPR are to be understood as references to the FADP;
- The competent supervisory authority shall be the FDPIC;
- References to ‘EU’, ‘Union’ and ‘Member State’ are replaced with ‘Switzerland’;
- In Clause 17, Option 1 shall apply. The Parties agree that the clauses shall be governed by the law of Switzerland;
- In Clause 18(b) the Parties choose the courts of Zurich, Switzerland as their choice of forum and jurisdiction.
- The Parties shall complete Annexes II–III below, which are incorporated in the Standard Contractual Clauses by reference.
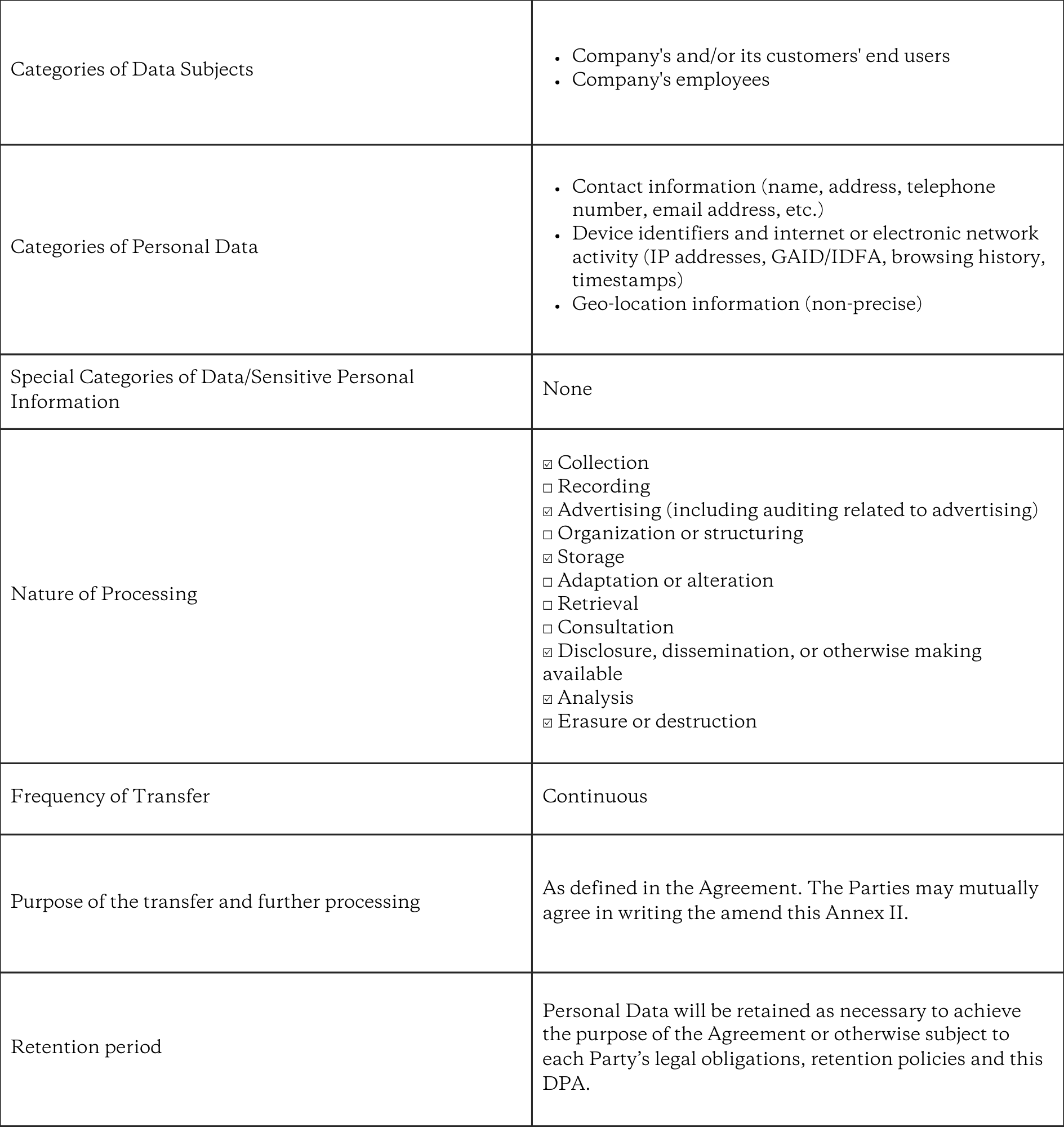
Annex II – Description of processing activities
A. Identification of Parties
"Data Exporter": the Company;
"Data Importer": the Recipient.
Description of Transfer
Annex III – Technical and Organizational Measures to Ensure the Security of the Data
Description of the technical and organizational measures implemented by the data importer (including any relevant certifications) to ensure an appropriate level of security, taking into account the nature, scope, context and purpose of the processing, and the risks for the rights and freedoms of natural persons.
Security Management
Recipient maintains a written information security management system (ISMS), in accordance with this Annex, that includes policies, processes, enforcement and controls governing all storage/processing/transmitting of Personal Data, designed to (a) secure Personal Data against accidental or unlawful loss, access or disclosure; (b) identify reasonable foreseeable and internal risks to security and authorized access to Recipient Network, and (c) minimize security risks, including through risk assessment and regular testing. The ISMS will include the following measures:
- Recipient actively follows information security trends and developments as well as legal developments with regards to the services provided and especially with regards to Personal Data and uses such insights to maintain its ISMS, as appropriate.
- To the extent Recipient process cardholder or payment data (such as payment or credit cards), Recipient will maintain its ISMS in accordance with the PCI DSS standard, augmented to cover Personal Data, or such other alternative standards that are substantially equivalent to PCI DSS for the establishment, implementation, and control of its ISMS. Additionally, Recipient will be assessed against PCI DSS annually by an on-site assessment carried out by an independent QSA (Qualified Security Assessor) and upon Company's request, not to exceed once annually, Recipient will provide Company with PCI DSS attestation of compliance.
Maintain an Information Security Policy
Recipient's ISMS is based on its security policies that are regularly reviewed (at least yearly) and maintained and disseminated to all relevant Parties, including all personnel. Security policies and derived procedures clearly define information security responsibilities including responsibilities for:
- Maintaining security policies and procedures;
- Secure development, operation and maintenance of software and systems;
- Security alert handling;
- Security incident response and escalation procedures;
- User account administration;
- Monitoring and control of all systems as well as access to Personal Data.
Personnel is screened prior to hire and trained (and tested) through a formal security awareness program upon hire and annually. For service providers with whom Personal Data is shared or that could affect the security of Personal Data a process has been set up that includes initial due diligence prior to engagement and regular (typically yearly) monitoring.
Personal Data has implemented a risk-assessment process that is based on ISO 27005.
Secure Networks and Systems
Recipient has installed and maintains a firewall configurations to protect Personal Data that controls all traffic allowed between Recipient's (internal) network and untrusted (external) networks, as well as traffic into and out of more sensitive areas within its internal network. This includes current documentation, change control and regular reviews.
Recipient does not use vendor-supplied defaults for system passwords and other security parameters on any systems and has developed configuration standards for all system components consistent with industry-accepted system hardening standards.
Protection of Personal Data
Recipient keeps Personal Data storage to a minimum and implements data retention and disposal policies to limit data storage to that which is necessary, in accordance with the needs of its customers.
Recipient uses strong encryption and hashing for Personal Data anywhere it is stored. Recipient has documented and implemented all necessary procedures to protect (cryptographic) keys used to secure stored Personal Data against disclosure and misuse. All transmission of Personal Data across open, public networks is encrypted using strong cryptography and security protocols.
Vulnerability Management Program
Recipient protects all systems against malware and regularly updates anti-virus software or programs to protect against malware – including viruses, worms, and Trojans. Anti-virus software is used on all systems commonly affected by malware to protect such systems from current and evolving malicious software threats.
Recipient develops and maintains secure systems and applications by:
- Having established and evolving a process to identify and fix (e.g. through patching) security vulnerabilities, that ensures that all systems components and software are protected from known vulnerabilities,
- Developing internal and external software applications, including web-applications, securely using a secure software development process based on best practices, e.g. such as code reviews and OWASP secure coding practices, that incorporates information security throughout the software-development lifecycle,
- Implementing a stringent change management process and procedures for all changes to system components that include strict separation of development and test environments from production environments and prevents the use of production data for testing or development.
Implementation of Strong Access Control Measures
"Recipient Network" means the Recipient's data center facilities, servers, networking equipment, and host software systems (e.g. virtual firewalls) as employed by the Recipient to process or store Personal Data.
The Recipient Network will be accessible to employees, contractors and any other person as necessary to provide the services to the Company. Recipient will maintain access controls and policies to manage what access is allowed to the Recipient Network from each network connection and user, including the use of firewalls or functionally equivalent technology and authentication controls. Recipient will maintain corrective action and incident response plans to respond to potential security threats.
Recipient strictly restricts access to Personal Data on a need to know basis to ensure that critical data can only be accessed by authorized personnel. This is achieved by:
- Limiting access to system components and Personal Data to only those individuals whose job requires such access; and
- Establishing and maintaining an access control system for system components that restricts access based on a user’s need to know, with a default “deny-all” setting.
Recipient identifies and authenticates access to all systems components by assigning a unique identification to each person with access. This ensures that each individual is uniquely accountable for its actions and any actions taken on critical data and systems can be traced to known and authorized users and processes. Necessary processes to ensure proper user identification management, including control of addition/deletion/modification/revocation/disabling of IDs or credentials as well as lock out of users after repeated failed access attempts and timely termination of idling session, have been implemented.
User authentication utilizes at least passwords that have to meet complexity rules, which need to be changed on a regular basis and which are cryptographically secured during transmission and storage on all system components. All individual non-console and administrative access and all remote access use multi-factor authentication.
Authentication policies and procedures are communicated to all users and group, shared or generic IDs/passwords are strictly prohibited.
Restriction of Physical Access to Personal Data
Any physical access to data or systems that house Personal Data are appropriately restricted using appropriate entry controls and procedures to distinguish between onsite personnel and visitors. Access to sensitive areas is controlled and includes processes for authorization based on job function and access revocation for personnel and visitors.
Media and backups are secured and (internal and external) distribution is strictly controlled. Media containing Personal Data no longer needed for business or legal reasons is rendered unrecoverable or physically destroyed.
Regular Monitoring and Testing of Networks
All access to network resources and Personal Data is tracked and monitored using centralized logging mechanisms that allow thorough tracking, alerting, and analysis on a regular basis (at least daily) as well as when something does go wrong. All systems are provided with correct and consistent time and audit trails are secured and protected, including file-integrity monitoring to prevent change of existing log data or generate alerts in case. Audit trails for critical systems are kept for a year.
Security of systems and processes is regularly tested, at least yearly. This is to ensure that security controls for system components, processes and custom software continue to reflect a changing environment. Security testing includes:
- Processes to test rogue wireless access points,
- Internal and external network vulnerability tests that are carried out at least quarterly. An external, qualified party carries out the external network vulnerability tests.
- External and internal penetration tests using Recipient's penetration test methodology that is based on industry-accepted penetration testing approaches that cover all the relevant systems and include application-layer as well as network-layer tests
All test results are kept on record and any findings are remediated in a timely manner.
Recipient does not allow penetration tests carried out by or on behalf of its customers.
In daily operations IDS (intrusion detection system) is used to detect and alert on intrusions into the network and file-integrity monitoring has been deployed to alert personnel to unauthorized modification of critical systems.
Incident Management
Recipient has implemented and maintains an incident response plan and is prepared to respond immediately to a system breach. Incident management includes:
- Definition of roles, responsibilities, and communication and contact strategies in the event of a compromise, including notification of customers,
- Specific incident response procedures,
- Analysis of legal requirements for reporting compromises,
- Coverage of all critical system components,
- Regular review and testing of the plan,
- Incident management personnel that is available 24/7,
- Training of staff,
- Inclusion of alerts from all security monitoring systems,
- Modification and evolution of the plan according to lessons learned and to incorporate industry developments.
Recipient has also implemented a business continuity process (BCP) and a disaster recovery process (DRP) that are maintained and regularly tested. Data backup processes have been implemented and are tested regularly.
Physical Security
Physical Access Controls
Physical components of the Recipient Network are housed in nondescript facilities ("Facilities"). Physical barrier controls are used to prevent unauthorized entrance to Facilities both at the perimeter and at building access points. Passage through the physical barriers at the Facilities requires either electronic access control validation (e.g., card access systems, etc.) or validation by human security personnel (e.g., contract or in-house security guard service, receptionist, etc.). Employees and contractors are assigned photo-ID badges that must be worn while the employees and contractors are at any of the Facilities. Visitors are required to sign-in with designated personnel, must show appropriate identification, are assigned a visitor ID badge that must be worn while the visitor is at any of the Facilities, and are continually escorted by authorized employees or contractors while visiting the Facilities.
Limited Employee and Contractor Access
Recipient provides access to the Facilities to those employees and contractors who have a legitimate business need for such access privileges. When an employee or contractor no longer has a business need for the access privileges assigned to him/her, the access privileges are promptly revoked, even if the employee or contractor continues to be an employee of Recipient or its affiliates.
Physical Security Protections
All access points (other than main entry doors) are maintained in a secured (locked) state. Access points to the Facilities are monitored by video surveillance cameras designed to record all individuals accessing the Facilities. Recipient also maintains electronic intrusion detection systems designed to detect unauthorized access to the Facilities, including monitoring points of vulnerability (e.g., primary entry doors, emergency egress doors, etc.) with door contacts, or other devices designed to detect individuals attempting to gain access to the Facilities. All physical access to the Facilities by employees and contractors is logged and routinely audited.
Continued Evaluation
Recipient will conduct periodic reviews of the Security of its Recipient Network and adequacy of its information security program as measured against industry security standards and its policies and procedures. Recipient will continually evaluate the security of its Recipient Network to determine whether additional or different security measures are required to respond to new security risks or findings generated by the periodic reviews.
Please find the previous version of this document, dated April 2025, here.